The 5 Cs Of Cybersecurity To Prevent Business Intrusion
Posted by: John / Posted on: August 1, 2021
Cybersecurity plays a pivotal role in the IT industry to protect any breach of data and preventing against theft of hardware, software, and electronic solutions. It is an essential element of IT affirmations to prevent meddling of protected data and prevent peeling into its levels without authorized roles. By protecting against digital attacks a robust model is ensured that encapsulates all the goodness of security and maintains data integrity. It has evolved over the past decades and now is a potent element of IT solutions. Without adopting a strong cybersecurity configuration in the business it becomes vulnerable to attacks and intrusion of external components.
With cybersecurity as a part of the business process, one doesn’t have to fret upon losses and can adopt a secure strategy to offer turnkey solutions to its vendors and customers with agile methodology. Cyber threats are reduced and internet-connected origins viz. software and hardware function securely and smoothly with a powerful cybersecurity model that exudes a protected environment. The cybersecurity model adheres to 5 Cs components which give an insight into the requisites of layout of a strengthened framework when abiding by secure structure.
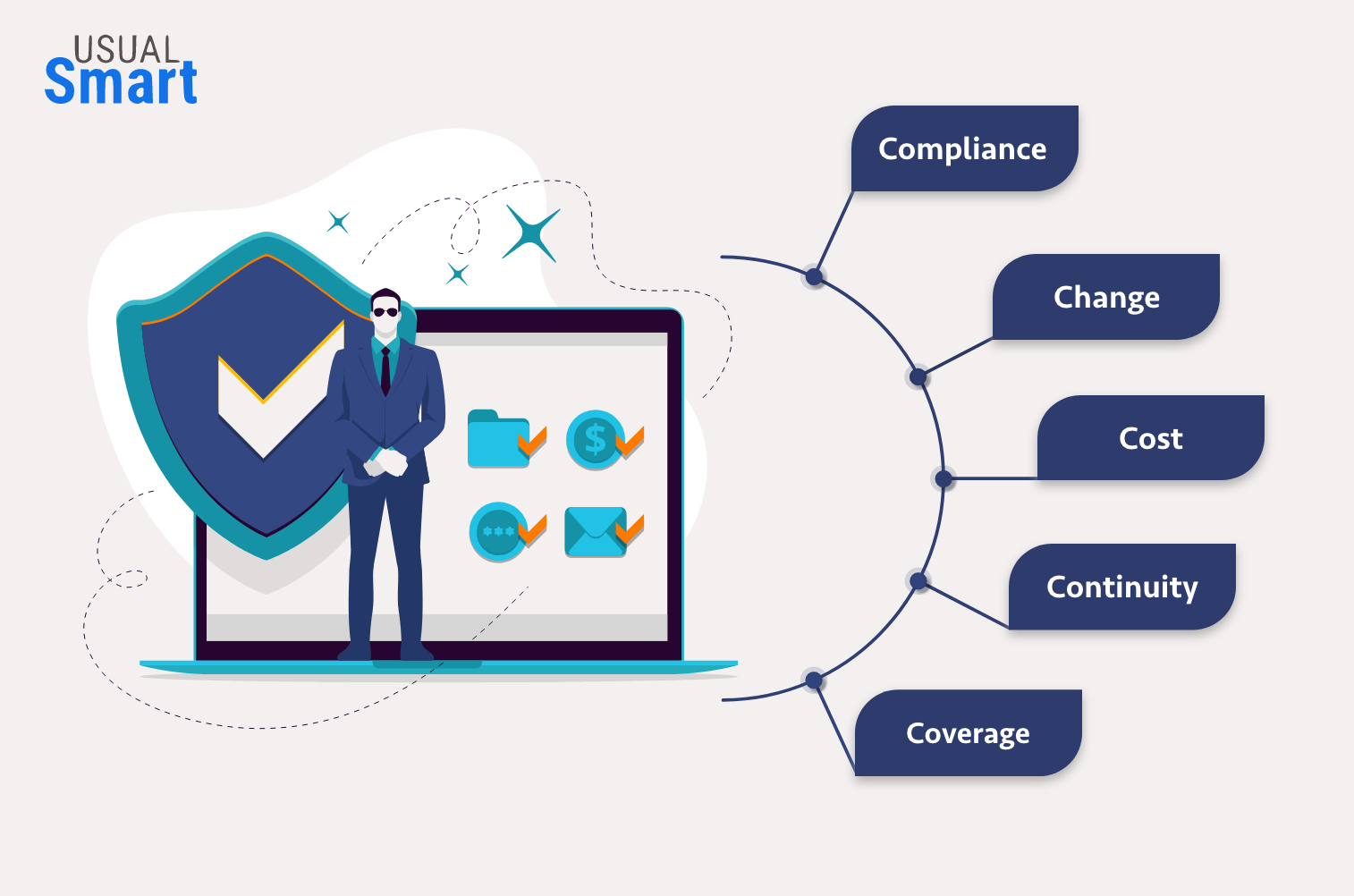
The 5 Cs are – Change, Compliance, Cost, Continuity, and Coverage.
Change – For an organization, there is an array of competitive threats from multiple sources in current scenario and therefore it becomes stringent to maintain new regulations and risk management to float up in the market and maintain a perpetual vigilance to beat the competition. Global redefinition has led to springing up of new organizations overnight and therefore strategies should be encompassed that tweak the business and maintain a strong cybersecurity department to beat the rivalry. As it is said – ‘Change is the only constant,’ it must be embraced with strict adherence. The business model should be deployed and retracted quickly to meet the outer alterations to add star-studded performance by the organization emphasizing the change adoption.
Compliance – Rules’ compliance stays at the heart of many organizations. Corporate risk management and compliance with the policies is a must to thrive methodically in the industry and beat the peripheral struggle to establish itself. Failing to obey the rule’s compliance can have a devastating impact on the organization and make it susceptible to cyber threats. Therefore, compliance threats become an intricate part of cybersecurity obeying which corporate threats can be evaded and a strict policy can be maintained to escape intrusion by outer elements. Compliance becomes an essential element of the cybersecurity world which lays the foundation for a safe environment of processes.
Cost – An organization’s capacity to establish itself in the industry largely relies on the customer front. Its survival strictly pivots on how the customer is addressed and delivered values. It is almost impossible to keep high costs and garner customers with the same intensity. Therefore, customers should be kept on a pedestal by lowering the cost of operations and delivery and investing more in maintaining a strong cybersecurity section by fine-tuning the policies to offer the best of both worlds to the customer. Here, cost for equipment must be lowered and strategies should be comprised that lead to a resilient business model that rebounds to its original or last state in case of failure of systems.
Continuity – A business continuity plan is an instrumental part of any organization to prevent loss of existence since fallouts are an inevitable part of business execution. Organizations chiefly spend a huge chunk of money to create backup plans and disaster recovery strategies neglecting the scenario of a major catastrophe if there is a massive invasion. Since these recovery plans are reliant on the internal structure of the fallout of the system the organization is left with nothing. Therefore, there is the necessity of a reliant business continuity plan that is resilient enough to bounce back to the original state of operations in case of cyber invasion. Cybersecurity is heavily reliant on such plans that enable a strict observance of security and fallouts in case of some upheaval.
Coverage – There is no better time to observe exponential growth in the market with the geographical expansion than now. Organizations are launching their franchise in multiple locations and increasing their customer base dispersion geographically. These expansions have hidden costs if not monitored meticulously therefore, small costs must be administered carefully to meet and beat the high financial risks at a later stage. A strategy should be dropped in to manage operations anywhere at any point in time and have high benefits. This also ensures adhering to a cost-effective pattern that incorporates a strict cybersecurity model.
Therefore, these were the 5 Cs that become stringent part of any business pattern to beat fallouts, cost risks and follow a resilient model at all times. It prevents threats against malware, cyber intrusion, ransomware, phishing, distributed denial of service (DDoS) attack, Man-in-the-middle (MitM) attack, and more. The most common sort of attacks is by malware like a virus, worms, Trojan horses, spyware, rootkits, adware, backdoor viruses key loggers. Having a detection plan for malware and other sorts of attacks can lower the imposition and build a strong protected system to combat these sorts of attacks.
These attacks or malware can be intruded on by automation measures as threat detection, threat response, and human augmentation and anti-virus software, firewalls, VPNs, and buying services with cybersecurity vendors like McAfee, CISCO, Microsoft, Avast, Quick Heal, and other reputed brands.